In today’s digital world, businesses are generating and storing vast amounts of sensitive data. When it comes to disposing of IT assets, such as computers, servers, and storage devices, businesses must ensure that their data is securely erased, and the equipment is disposed of in an environmentally responsible manner. However, in addition to these challenges, businesses must also ensure that the chain of custody is secure. A secure chain of custody is critical to ensuring that sensitive data is protected from unauthorized access, theft, or loss. In this blog post, we’ll discuss the importance of a secure chain of custody during the ITAD process and how businesses can ensure that their data is secure at every stage of the asset disposition process.
What is a chain of custody?
In the context of IT asset disposition, the chain of custody is used to track the movement of IT assets from the business’s premises to the ITAD vendor’s facility and back.
Why is a secure chain of custody important?
A secure chain of custody is essential because it provides businesses with a record of who has had access to their IT assets and when. This is important because it ensures that the assets are handled and disposed of in a manner that is consistent with the business’s security and privacy policies. A secure chain of custody also provides businesses with the peace of mind that comes with knowing that their sensitive data is protected from unauthorized access or theft.
A secure chain of custody is a critical component of the ITAD process, ensuring that sensitive data is protected at every stage of the asset disposition process. This process involves the tracking of the movement and handling of assets containing sensitive data from the moment they are decommissioned until they are finally destroyed. A secure chain of custody helps businesses to maintain control over their assets and to minimize the risk of data breaches.
How can businesses ensure a secure chain of custody during the ITAD process?
There are several steps that businesses can take to ensure a secure chain of custody during the ITAD process. These include:
- Partner with a reputable ITAD vendor – Partnering with a reputable ITAD vendor is critical to ensuring a secure chain of custody. A reputable vendor should have strict security protocols in place to protect your data and assets throughout the disposition process. Look for a vendor that is certified by recognized organizations, such as the National Association for Information Destruction (NAID) and one who uses certified software to destroy the data and has a proven track record of providing secure IT asset disposition services.
- Develop a clear chain of custody policy – Developing a clear chain of custody policy is essential to ensuring that all stakeholders understand their roles and responsibilities. Your policy should outline the steps that must be taken to maintain a secure chain of custody, including who is responsible for the assets at each stage of the process, how they will be transported, and how they will be tracked.
- Make sure ITAD vendor uses tracking technology – When you hire an ITAD make sure they are using tracking technology, such as GPS tracking, RFID tags, or barcodes, that can help you maintain a secure chain of custody. These technologies allow you to track your assets’ movements in real-time, providing you with visibility into their location and status.
- Conduct regular audits – Regular audits to the ITAD vendor facility can help you identify any gaps in your chain of custody policy and address them before they become a problem. Your audits should include a review of your policy, as well as physical checks of your assets to ensure that they are where they should be.
- Make sure ITAD vendor employees are trained – ITAD employees need to be trained on the importance of a secure chain of custody and how to follow your policy is essential to ensuring that your assets are handled properly. Make sure that all employees who are involved in the disposition process receive training and that they understand their role in maintaining a secure chain of custody.
A secure chain of custody is critical to ensuring that businesses’ sensitive data is protected during the ITAD process.
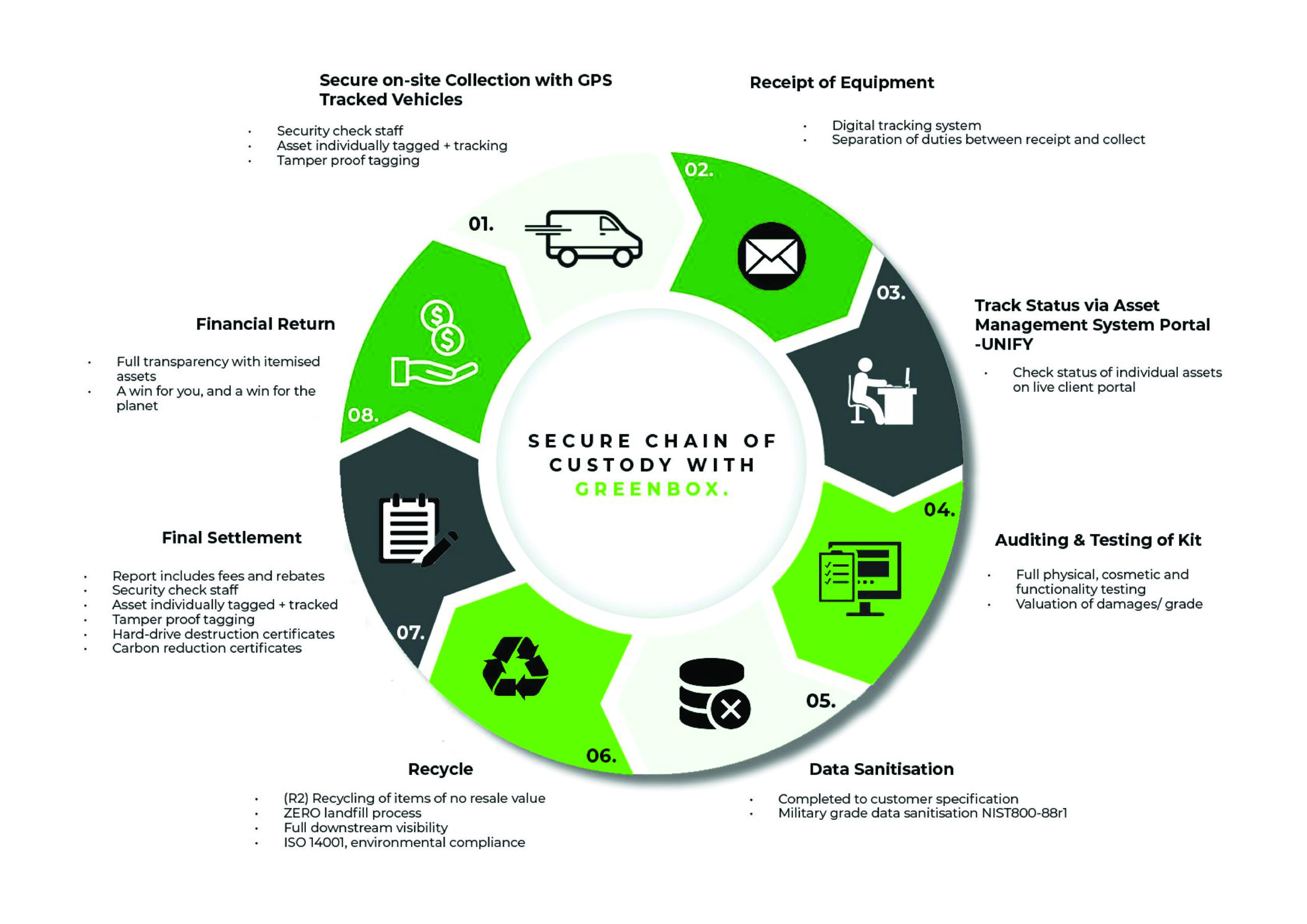
Greenbox’s secure chain of custody includes secure on site collection with GPS Tracked Vehicles, track status of your equipment via Unify, auditing and testing of the equipment, secure data sanitisation (Blancco), Recycle the assets, Final settlement with reports and certificates at every stage and a secure financial return which is a win for you and a win for the planet.